
PROTECT WHAT
MATTERS MOST
Let us identify vulnerable areas in your organisation’s security in order to rectify them.
MOBIUS BINARY
SERVICES
Our services focus on cyber threat intelligence, penetration testing, and ethical hacking. By thinking like hackers, we perform real-world simulations to identify gaps and help you protect your digital boundaries.
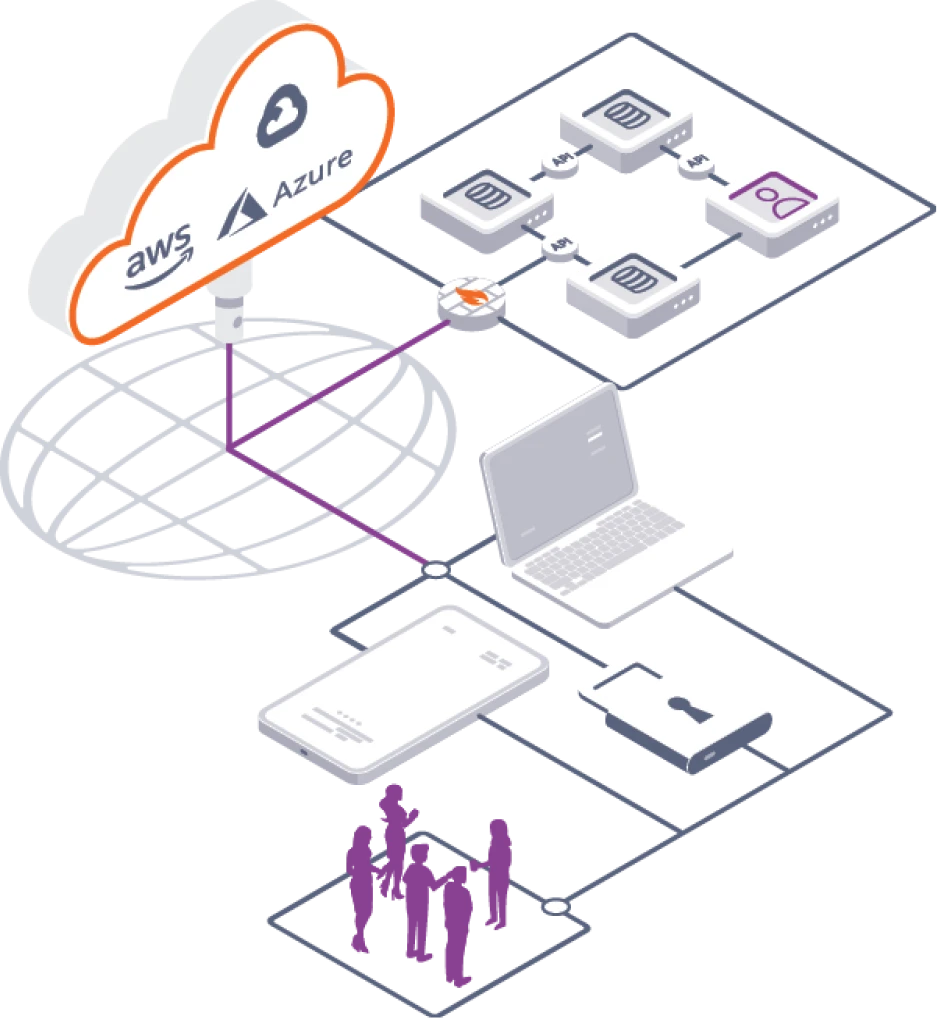
In this exercise we conduct a holistic reconnaissance of your organisation to determine your defence and depth controls.
An external penetration test considers a potential attack from outside your organisation. Can an attacker breach your perimeter controls to access the internal network?
Internal penetration testing is carried out in the context of an attacker having access to your network. How would they be able to establish a foothold? Would they be able to move laterally? Access sensitive information? Escalate their privilege to gain control of your network?
We’ll test your defences from the outside in, examining every layer along the way.
What can happen to the application on the device? And what can happen when interacting with it?
First we look at what an attacker could do with the application on the device itself. Does it securely store sensitive data on the device and prevent unauthorised access to the data? Can it be tampered with?
Then we see how the application connects to the back-end servers. Can traffic be intercepted and manipulated?
Our approach is aligned to the OWASP Mobile Application Security Testing Guide (MASTG): “a comprehensive manual for mobile app security testing and reverse engineering”.
Testing from an unauthenticated perspective identifies whether an attacker without credentials can access the web application and any of the related data or functionality they’re not authorised to access.
From an authenticated perspective, can a user access functionality they shouldn’t, such as escalating their privileges to access other users’ data or administrative functionality?
Our approach is aligned to the OWASP Web Security Testing Guide (WSTG): “a comprehensive guide to testing the security of web applications and web services”.
APIs underpin the communication between systems within your organisation and third-party systems outside it. Many of the security vulnerabilities that affect web and mobile applications can be exploited via direct manipulation of API calls.
It’s common for developers to implement security or functionality controls in the front end of web and mobile applications, but these controls are often not applied to the associated API calls – hence the need to test them thoroughly.
Humans have the best intentions. That makes them easy targets. Manipulating users can bypass even the most rigorous defences, and in many cases social engineering has been the initial step in attacks that have resulted in significant breaches.
Testing your users is just as critical as testing your other defences. Our social engineering expertise can either be used as part of a red team exercise or as part of a standalone campaign to gauge the potential impact of an attack.
We dive deep into your cloud environment, mimicking real-world threats to identify critical vulnerabilities. Our comprehensive approach covers everything from weak passwords and insecure data to misconfigured firewalls.
Let Mobius Binary protect your business with expert penetration testing for Microsoft Azure, Google Cloud, and AWS.
To protect your organisation effectively against cyber-attacks, you must first know which tactics, techniques, and procedures will most likely yield results for an attacker and whether you would manage to detect, prevent or respond appropriately.
Our Technical Threat Simulation is based on the MITRE ATT&CK framework and uses various tools and scripts to automate the simulation of these tactics, techniques, and procedures against your organisation.
The result is that you can determine whether your security controls are effective against real-world attacks and pinpoint any weaknesses, allowing you to drive improvements in your security posture.
Building your defences isn’t good enough any more. Cyber Threat Intelligence helps you identify publicly available information about your organisation so you can prevent or mitigate attacks.
This information can include credentials in breached databases, sensitive data stored in code repositories, conversations on the dark web or deep web, and your exposed attack surface (including infrastructure you’re not aware of).
As an added benefit, our service helps to protect your brand by identifying instances of domain and social media impersonation, which could impact your reputation.
Case studies

Permission to Launch in a Fintech Startup
Another example of ongoing support, we’re currently helping a...➜

Guarding the Guard in a Tech Startup
For three years running, we’ve performed web application...➜

Business As Usual in the Banking Sector
Along with standalone projects, we’re also able to work...➜

Unsafe Objects in the Retail Industry
Working as subject matter experts within the internal audit...➜

Beware the Black Swan
Here’s a useful example of our work with Mobius...➜

One in a Thousand
An oil and gas company with global operations required...➜

Unintentional Discount in the Retail Industry
A large retailer with an e-commerce solution asked us...➜

The Talkative Chatbot in the Banking Sector
A bank with operations across multiple African countries asked...➜

Reassurance in the Insurance Industry
A large insurer asked us to perform a wide...➜

Excavation becomes A SERIOUS PROSPECT
A listed gold mining company asked us to perform an...➜

From Weak Spots to Fort Knox
A retail client partnered with Mobius Binary to enhance...➜
Thought Leadership
The Mobius Group 2022 Cyber Security Survey

The path to digital trust

our Team
Our security analysts are all highly skilled individuals with industry-leading certifications. We have a wealth of experience testing various technologies and environments from different perspectives to ensure you are clearly secure. The team is led by Graeme, Rob, Rex and Andre.

Graeme Huddy
Director
Graeme is experienced in information security, cyber security, IT management and information... assurance across multiple industries in both the private and public sectors. Besides being responsible for operations management and the consistent quality of our services, Graeme understands that managing risk is just one of an organisation's business challenges. He ensures that you tackle what’s most important, communicating technical findings in the context of the actual risk and potential impact.

Rob Len
Technical Head of Security Testing
With a lifelong curiosity around how things work, Rob has become an expert in all facets of... penetration testing. He has a deep technical understanding, the ability to explain complex challenges in plain language, and a binary view on whether or not a vulnerability is a risk to your business. Rob is responsible for technical quality assurance and guides our analysts to bring out the best in our team, ensuring all angles are covered.

Rex Hart
Penetration Testing Service Delivery Manager
Rex is the glue that binds our penetration testing. As the primary point of contact for our clients..., he makes sure you get everything you want when you need it, and he’s the key facilitator when it comes to any of our tests. Rex schedules our scoping calls, plans our project delivery, performs initial quality assurance, and keeps clients up to date on progress. As the go-to guy for Mobius Binary, he’s the one you’ll have on speed dial.

Andre Viviers
Cyber Threat Intelligence Service Delivery Manager
Andre is experienced in information technology management and risk, information and... cyber security, data protection and privacy, and information assurance across multiple industries. Andre is responsible for the delivery of the Mobius Binary Threat Intelligence service, which includes brand protection. This service aims to assist our clients to understand their threat landscape and how to respond to these threats.



